supply chain discovery
See what you're really connected to
Map the domains, APIs, and suppliers that make up your extended attack surface. Gain the context to prioritize risks, and take action before attackers do.

supply chain discovery
See what you're really connected to
Map the domains, APIs, and suppliers that make up your extended attack surface. Gain the context to prioritize risks, and take action before attackers do.


































Assets appear, vendors change, configurations drift, and attackers adapt. Our recon is a continuous cycle: find what’s new, understand how close it sits to your critical systems, validate resilience, and monitor for shifts in security postures.




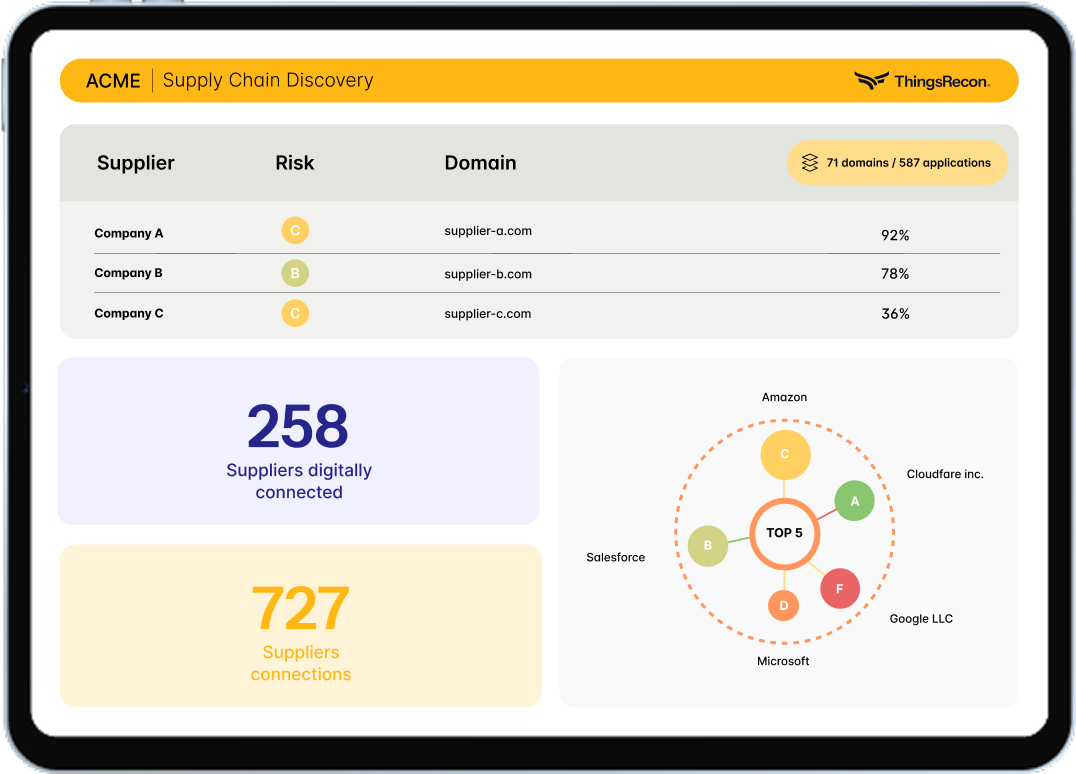
Any tool can map what’s out there. We show you
how close it sits to your core.
ThingsRecon’s signature metric Digital Proximity™ (Patent Pending) measures how deeply a third-party or asset is integrated into your digital surface — technically, operationally, and contextually.
If a vulnerability rated as medium by CVSS sits on a public-facing asset that’s tightly integrated with a high-value business system… it’s critical to you.
A shared login page, a forgotten app, a misconfigured script, an unseen redirect... if it touches your ecosystem, we’ll show you how, where, and why it matters.
Employees often introduce tools outside the approved process — whether for analytics, chat, or productivity. ThingsRecon surfaces embedded third-party scripts, DNS entries, and integrations to reveal shadow SaaS that could pose compliance or security risks.
Your digital surface changes constantly. So does your vendors’. We monitor and prioritize suppliers based on their live exposure across the internet, helping you respond fast to new vulnerabilities or exposed assets.
When acquiring or merging with another company, understanding inherited third-party risk is critical. ThingsRecon maps both direct and indirect vendor exposure, helping you avoid surprises during integration.
How security teams use supply chain discovery.


We were surprised by the level of ‘things’ discovered—far greater than any other solution we have used or tested.
ThingsRecon helps Northumbria NHS focus our security approach based on evidenced exposure. And they have worked with our team really closely to quickly prioritise and address risks.”

Simon Sleightholm
Information Assurance & Security Manager
Northumbria Healthcare










Everything you need to know about ThingsRecon Supply Chain Discovery.
Supply chain discovery is the continuous process of identifying, mapping, and monitoring your digital exposure through third-party vendors, services, and integrations. It helps you understand where your organization might be vulnerable through external connections.
Modern organizations rely on a web of suppliers, SaaS tools, and service providers. Each one adds potential risk. Without visibility into how those connections expose you, it's nearly impossible to manage third-party risk effectively, let alone comply with regulatory requirements.
ThingsRecon analyzes domains, scripts, APIs, and IPs to detect supplier-linked assets and exposures. Using proprietary proximity and context insights, we discover your extended ecosystem and show you which suppliers are most integrated—and therefore riskiest.
Digital proximity is our way of measuring how closely a supplier is embedded into your environment—technically, operationally, or through shared infrastructure. This helps you prioritize based on real exposure, not just theoretical risk.
Yes. Supply Chain Discovery helps meet regulatory expectations under frameworks like DORA, NIS2, and SEC incident reporting, by giving you continuous visibility and defensible, risk-based assessments.
Our platform performs continuous discovery and monitoring. Unlike solutions that sacrifice speed for depth, our AI-driven algorithms pivot across multiple datasets, enabling us to discover more without slowing down. Supplier-linked exposures and changes in your extended surface are surfaced in near real-time.
No. ThingsRecon is completely agentless and non-intrusive, meaning no installs or internal access are needed to start mapping your supply chain exposure.
From marketing tech and cloud service providers to hosting infrastructure and niche software tools—if a supplier touches your digital surface, we’ll show you where and how.
