ATTACK SURFACE DEEP DISCOVERY
Own your extended ecosystem
Identify unknown assets and reduce exposure with continuous discovery and context-based insights.


ATTACK SURFACE DEEP DISCOVERY
Own your extended ecosystem
Identify unknown assets and reduce exposure with continuous discovery and context-based insights.


Deeper, multi-vector discovery that surfaces up to 50% more assets, and full supply chain mapping, with economic, political and operational context
Cyber & Business risk, financial solvency,
geopolitical instability, compliance gaps, and supply chain interdependencies
Actionable intelligence on vulnerabilities
+ multi-criteria prioritization blending cyber severity + business impact + third-party proximity & connectivity

Built for continuous external surface visibility and business-aligned prioritization, so you can address risk before it scales.
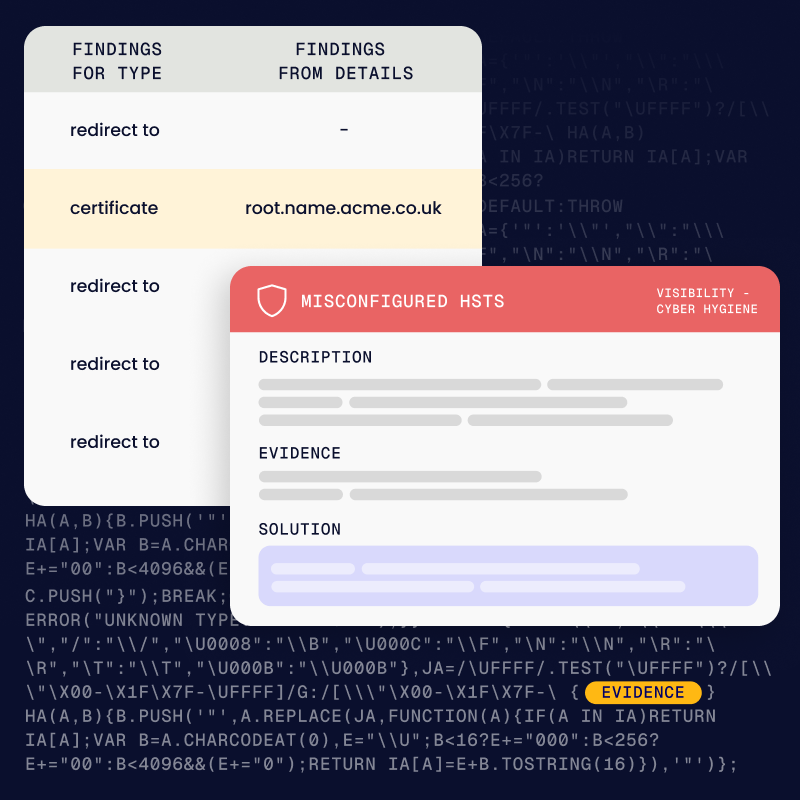
Leverage over 100 hygiene indicators to assess exposure, business criticality, and asset proximity. You’ll find domains, IPs, APIs, cloud assets, shadow applications & legacy test tools, expired or misconfigured controls, and more.

Risk is measured across three dimensions: visibility, hygiene, and attack vectors, with context, relationships, and asset concentration highlighting where risks matter most.

Not all tools catch what's hidden by geo-fences. ThingsRecon scans from regional vantage points to surface restricted portals, edge-cache differences, and geo-based content changes, thus avoiding regional blocking.

Always-on scans detect new assets, misconfigurations, and changes the moment they appear. With real-time alerts and audit-ready reports, you gain speed in response and confidence in what you report.
Every new cloud account, app rollout, or digital project creates fresh exposures. Deep discovery finds assets the moment they appear, so you can proactively manage your expanding attack surface.
Penetration tests are only as good as the assets in scope. Deep Discovery expands that scope by revealing forgotten subdomains, APIs, and shadow endpoints that human testers often miss.
When an alert hits, seconds matter. Deep Discovery shows which systems, suppliers, and data are connected, giving your team instant blast-radius mapping to accelerate containment.
Regulators expect continuous proof, not point-in-time scans. Deep Discovery delivers audit-ready evidence of your external posture: trendlines, hygiene scores, and remediation timelines aligned to GDPR, HIPAA, NIS2, and DORA.
.png)


Most external attack surface tools stop at known domains, active subdomains, common IP ranges. But attackers connect the dots across forgotten infrastructure, shadow SaaS, inherited vendor systems, and misconfigured cloud assets.
Our deep discovery approach uncovers up to 50% more assets than traditional EASM platforms (as told by our customers). This means:

































We were surprised by the level of ‘things’ discovered—far greater than any other solution we have used or tested.
ThingsRecon helps Northumbria NHS focus our security approach based on evidenced exposure. And they have worked with our team really closely to quickly prioritise and address risks.”

Simon Sleightholm
Information Assurance & Security Manager
|
Northumbria Healthcare
Everything you need to know about ThingsRecon Attack Surface Discovery.
Deep attack surface discovery finds assets and exposures that EASM tools often miss: from forgotten subdomains and cloud endpoints to shadow SaaS and inherited infrastructure. In addition to listing what’s out there, it adds context with Digital Proximity™ (Patent Pending), showing which exposures are closest to your critical systems. The result is a more complete, prioritized view of your external posture, giving you confidence that hidden risks aren’t slipping through the cracks.
Everything that touches your ecosystem. Applications (e.g., web applications, SSH servers, databases), API endpoints (URIs callable by a program), certificates (SSL digital entity’s identity), cookies, domains, FQDNs, headers, inputs (web application fields expecting data from the user), IPs and IP ranges, mobile apps, cloud apps, scripts (JavaScript locations)... Talk to us if you’re interested in the full breadth of our recon.
No, all discovery is performed externally. No agents installed, non-intrusive scanning.
Pricing is based on number of domains and scan frequency: weekly, monthly, quarterly, or annually. Contact us to get a custom quote.
Our platform performs continuous discovery and monitoring. Unlike solutions that sacrifice speed for depth, our AI-driven algorithms pivot across multiple datasets, enabling us to discover more without slowing down. Supplier-linked exposures and changes in your extended surface are surfaced in near real-time.
Yes. ThingsRecon discovery data can be integrated into SIEM, SOAR, ticketing, and GRC workflows.
