Supply Chain Intelligence
The first living map of your
extended digital ecosystem
Discover hidden connections, measure Digital Proximity™ to your crown jewels, and prioritize risks using AI-driven intelligence.
Supply Chain Intelligence
The first living map of your
extended digital ecosystem
Discover hidden connections, measure Digital Proximity™ to your crown jewels, and prioritize risks using AI-driven intelligence.
Deep discovery finds domains, IPs, APIs, certificates, shadow apps and supplier infrastructure others miss (up to 50% more findings).
Digital Proximity™ and Trust badges show which suppliers sit closest to your crown jewels so you fix what threatens the business.
Agentic BI adds financial, geopolitical, compliance, and OSINT signals; configurable report templates deliver audit-ready evidence.
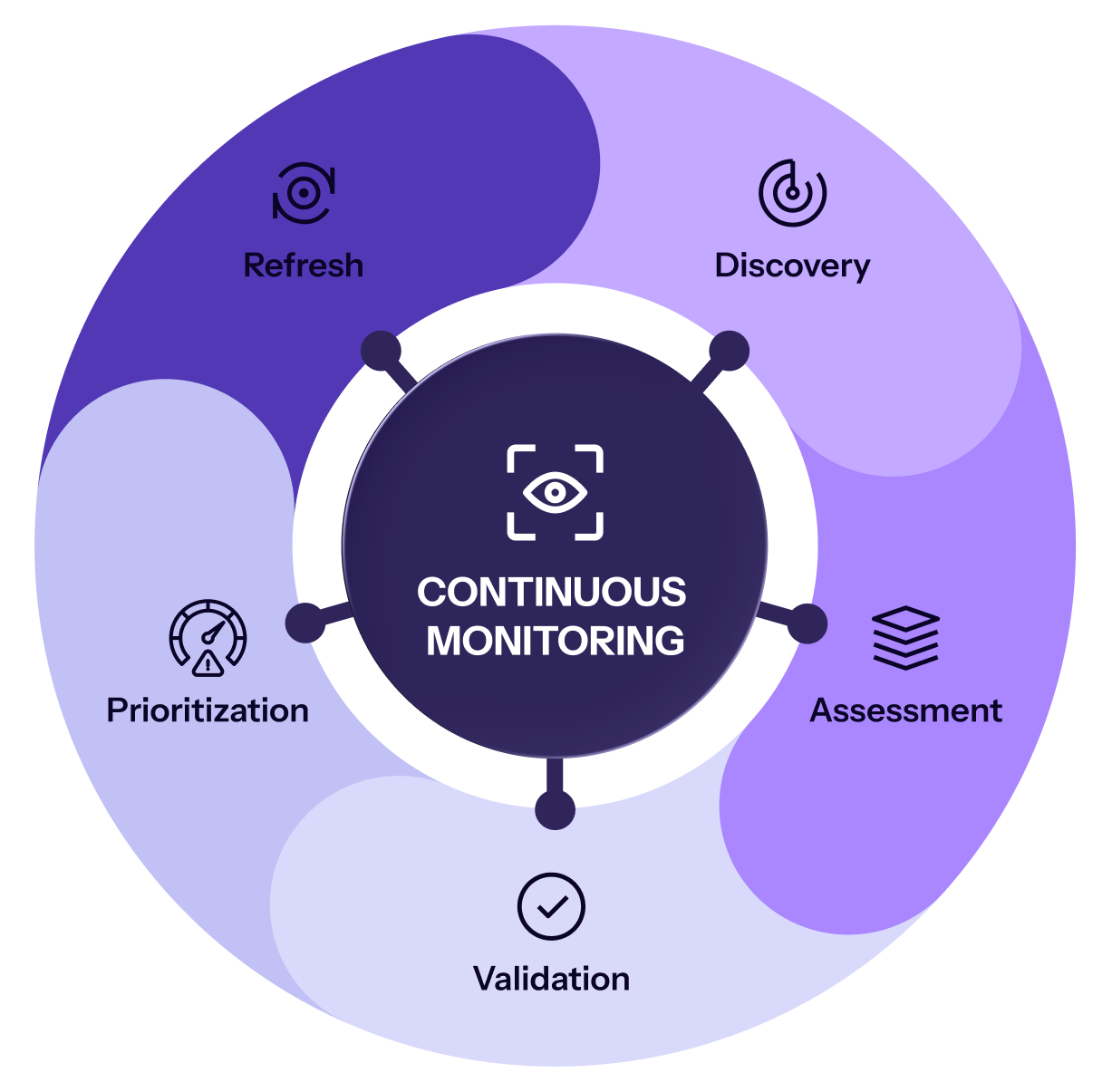
Assets appear, vendors change, and attackers adapt. ThingsRecon continuously helps you find what’s new, see how close it is to your critical systems, validate resilience, and monitor for shifts in posture.

Uncovers exposed assets, including inherited vendor infrastructure, forgotten tooling, and shadow risk.

Scores vendors by exposure and business criticality, mapping Digital Proximity™ to show who’s most deeply embedded in your operations.

Identifies weak spots like outdated logins, insecure APIs, and misconfigurations, giving you a clear resilience scorecard.

Prepares GRC-ready reports and tracks changes over time with continuous scans and real-time alerts.

Employees often introduce tools outside the approved process — whether for analytics, chat, or productivity. ThingsRecon surfaces embedded third-party scripts, DNS entries, and integrations to reveal shadow SaaS that could pose compliance or security risks.
Your digital surface changes constantly. So does your vendors’. We monitor and prioritize suppliers based on their live exposure across the internet, helping you respond fast to new vulnerabilities or exposed assets.
When acquiring or merging with another company, understanding inherited third-party risk is critical. ThingsRecon maps both direct and indirect vendor exposure, helping you avoid surprises during integration.
Regulations like NIS2, DORA, and the SEC disclosure requirements demand continuous oversight of supply chain risk. Our discovery-first model helps you demonstrate proactive vendor monitoring with mapped connections.
How security teams use supply chain intelligence.
































Everything you need to know about ThingsRecon Supply Chain Intelligence.
We perform an external-only automated scan of the domain you provide and return a sample snapshot showing discovered assets and a supplier proximity view.
No. Our discovery is agentless and external.
Sample reports are delivered within 48–72 hours after verification.
Yes. We have points of presence in North America and Europe.
It measures how directly a supplier’s systems touch your most critical systems, so you can prioritize fixes by business impact.